“Phishing” can mean different things to different people. We use the term in a broad sense to encompass all socially engineered email attacks, regardless of the specific malicious intent (such as directing users to dangerous websites, distributing malware, collecting credentials and so on).
Here are a few of the other terms we use throughout this report and how we define them:
Bulk phishing: indiscriminate, “commodity” attacks in which the same email is sent to many people within an organization.
Spear phishing: Targeted attacks sent to selected people within an organization.
Whaling: Attacks against high-value targets, such as top executives.
Smishing: Attacks that use mobile text messaging (SMS) as the main communication vector.
Vishing: Attacks that use phone calls or voice messages to lure targets.
Phishing attacks on the rise
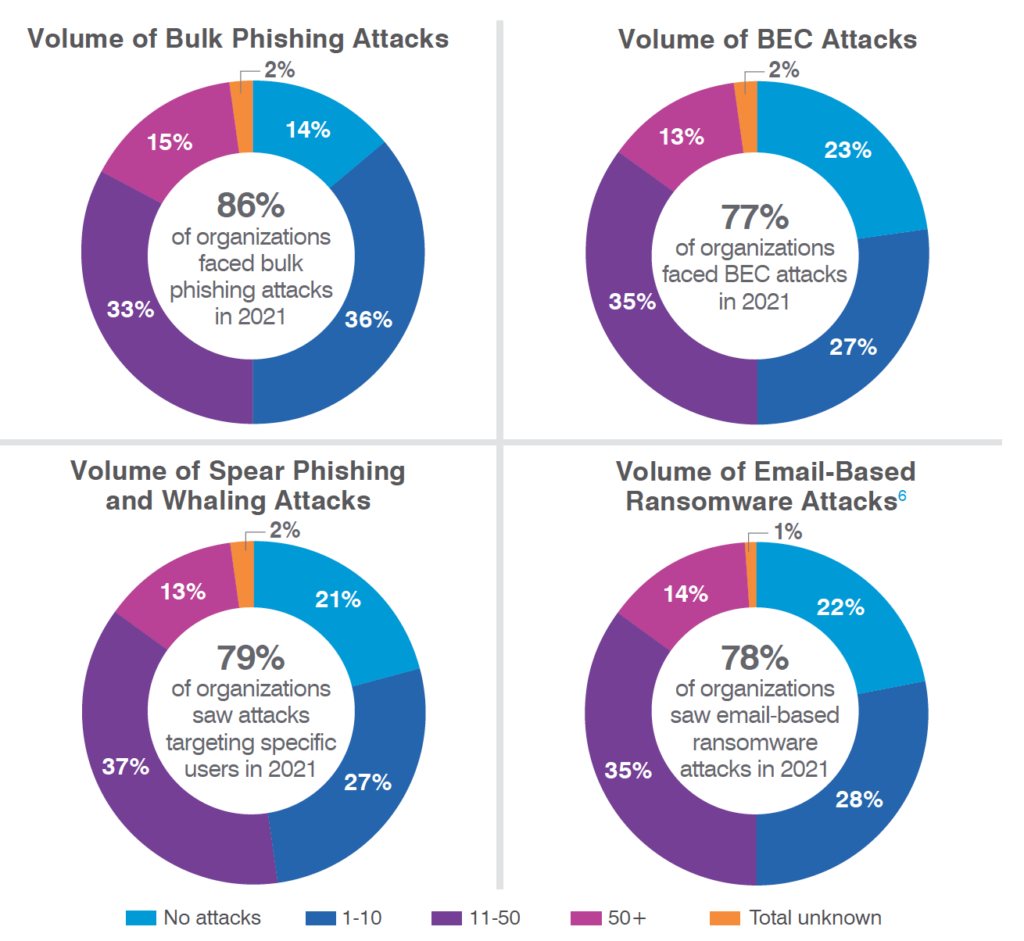
According to respondents, the 2021 threat landscape was more active than 2020’s. Reports of phishing attacks were up across the board. Indiscriminate “bulk” phishing attacks rose 12% year over year. And increases in targeted attacks were even higher: reports of spear phishing/whaling and business email compromise (BEC)—which includes payroll redirect and supplier invoicing fraud—were up 20% and 18%, respectively.5 Note: the figures represented in Figure 2 include both successful and unsuccessful attacks.
For the complete 60-page report, contact us.
